Your App Takes 8 Minutes to Hack. Your Protection Takes 60 Seconds.
Professional hackers can compromise an unprotected mobile app in under 10 minutes. Here's their exact playbook and how to shut it down in 60 seconds.
October 27, 2025
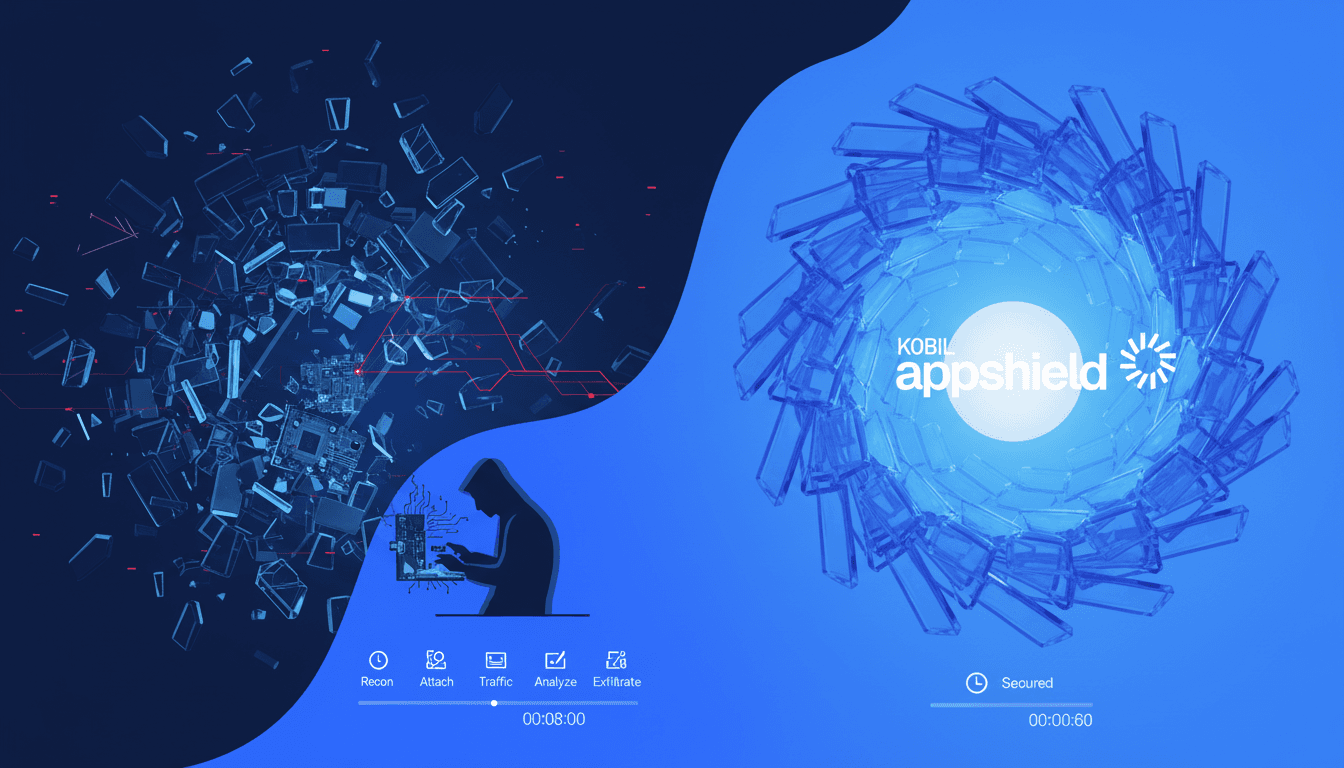
A professional penetration tester can break into your app in 8 minutes.
Not 8 hours. Not 8 days.
8 minutes.
Here's their exact playbook minute by minute.
The 8-Minute Attack Timeline
Minute 1: Reconnaissance
Download your APK from Play Store or IPA from App Store
Check app size, permissions, SDK versions
Identify if basic protections exist (root detection, SSL pinning)
Tool used: APKTool, Class-dump
Minute 2: Device Preparation
Launch app on rooted Android device (Magisk installed)
Or jailbroken iPhone (checkra1n)
Check if app detects root/jailbreak
90% of apps don't → proceed to next step
Tool used: Magisk Hide, Liberty Lite
Minute 3: Debugger Attachment
Attach debugger to running app
Check if anti-debugging is active
85% of apps don't block debuggers → full memory access gained
Tool used: Android Studio Debugger, lldb
Minute 4: Dynamic Instrumentation
Inject Frida into app runtime
Hook into sensitive functions (login, payment, API calls)
80% of apps have no Frida detection → game over
Tool used: Frida, Objection
Minute 5: API Traffic Interception
Set up proxy to intercept HTTPS traffic
Check for SSL pinning
70% of apps have weak or no SSL pinning → all API calls visible
Tool used: Burp Suite, Charles Proxy
Minute 6: Code Analysis
Decompile app to read source code
Search for hardcoded secrets (API keys, tokens, passwords)
60% of apps have secrets in code → backend access gained
Tool used: jadx, Hopper Disassembler
Minute 7: Memory Dump
Extract app memory during runtime
Find session tokens, user credentials, encryption keys
All stored in plain text for most apps
Tool used: Fridump, GameGuardian
Minute 8: Exfiltration
Copy user data from local storage
Clone session tokens to impersonate users
Access backend with stolen API keys
Attack complete. App fully compromised.
What Just Happened?
In 8 minutes, an attacker:
Bypassed your authentication
Stole user credentials
Intercepted API traffic
Accessed your backend
Extracted sensitive data
Gained persistence for future attacks
And your app never detected a thing.
Why Most Apps Fall in Under 10 Minutes
Because they rely on security theater measures that look secure but don't actually stop attacks:
"Protection" | Why It Fails |
"We use HTTPS" | Doesn't stop memory dumps or local storage access |
"Code is obfuscated" | Slows attackers by 2 minutes, doesn't stop them |
"We have basic root detection" | Magisk Hide bypasses it in 10 seconds |
"Login requires password" | Frida hooks bypass authentication logic |
"We don't store data locally" | Session tokens in memory are enough |
If an attacker can:
Run your app on a rooted device → They win
Attach a debugger → They win
Use Frida → They win
One vulnerability is all they need.
The 60-Second Defense
Here's what changes when you protect your app with AppShield Security Box:
Minute 1: Reconnaissance
Attacker downloads your app → Sees Security Box signature, knows it's hardened
Minute 2: Device Preparation
Launches on rooted device → App detects root + Magisk, refuses to run
Minute 3: Debugger Attachment
Tries to attach debugger → Anti-debugging active, process terminates
Minute 4: Dynamic Instrumentation
Injects Frida → Frida detection triggers, app shuts down
Minute 5-8: Nothing
Attacker gives up and moves to easier target.
One Click. 18 Protection Layers.
Security Box adds:
Device Security:
Root/Jailbreak Detection
Emulator Detection
Magisk Detection
Device Binding
App Security:
Anti-Debugging
Anti-Code Injection
Frida Detection
App Integrity Check
SSL Pinning
Code Obfuscation
Anti-Tampering
UI Security:
Screen Capture Protection
Screen Recording Prevention
Keylogger Protection
Tapjacking/Clickjacking Prevention
Remote Control Prevention
Automation Tool Detection
All in 60 seconds. Zero code changes.
The Math Is Simple
Time to hack an unprotected app: 8 minutes
Time to protect your app: 60 seconds
Which timeline do you prefer?
Don't Give Hackers 8 Minutes
See exactly what protections your app is missing.
Run a free security scan. Get your report in 60 seconds.
Then decide if 8 minutes is too long to wait.




